|
|
|
|
|
| |
| Mail Protect FAQ's
|
|
| |
|
| 1. Service Subscription FAQ’s |
| 1.1 |
What is Mail Protect Service? |
| |
Mail protect acts as a security layer between the internet and your email server 24x7, 365 days basis. Mail Protect redirects all your mail traffic (SMTP) through highly advanced, robust anti-spam and anti-virus screening setup and forwards only clean mails to your mail system. It also delivers your outbound e-mail via a secure, managed gateway protecting your e-mail servers at backend.
|
| 1.2 |
Will Mail Protect service be of any use when I already have mail security setup at my end? |
| |
Yes. Even if you continue to run your complete email security setup at your own end, Mail Protect service still makes good sense. Mail Protect benefits far outweigh the cost of service by offering huge savings on mail server space, time, and bandwidth .
Few benefits are;
Parameters |
Mail Protect Service Benefit |
Scalability & Redundancy |
- Mail Protect acts as DR Setup for your inbound messages.
- Unlimited queue management for up-to 5 days
- 99% Guaranteed ensures Zero Mail loss Guarantee
- Pay as per your user account requirement
|
Network Protection |
- All viruses and spam are cleaned at gateway level thus offering clean email traffic
- Optimum utilisation of Internet pipe
|
24x7 Access to technical resources |
- Service offers complete protections for both your inbound and outbound traffic.
|
GIDC believes that the first line of defense for virus/spam detection and prevention should start at the Internet gateway, where a virus/spam can be stopped before it enters the corporate network, minimising the chance of business-critical systems being infected.
|
| 1.3 |
How am I assured of service effectiveness? What reports are available? |
| |
Weekly and monthly report of all the messages sent, virus and spam cleaned and various other parameters report will be sent to you via email for further in-depth analysis on cost and resource savings.
|
| 1.4 |
I have outsourced my email services from some other service provider; can I still use Mail Protect for e-mail security? |
| |
Yes. Mail Protect service can secure your messaging system whether it is in-house or hosted by a third-party service provider. Only condition is that you must have a dedicated domain in order to use the service. You just need to change your MX record to point to Mail Protect System first; the system then forwards clean e-mails to any server you designate.
Please be advised that in few circumstances, Mail Protect may not be able to provide you outbound mail protection due to third party mailing setup limitations.
|
| 1.5 |
Do I need to change existing e-mail setup or security setup to utilise Mail Protect Service? |
| |
No. There is no need to change anything in your existing mail setup. Only change of your MX record is required to redirect all mails to Mail Protect Systems.
|
| 1.6 |
My e-mail setup is hosted at some other service provider. Can I still use the Mail Protect for e-mail security?
|
| |
Your messaging system can be in-house or hosted by a third-party service provider. Please note that you must have a dedicated domain in order to use the service. Your e-mail exchange records only need to point to our system first; the system then forwards clean e-mails to any server you designate.
|
| 1.7 |
How Mail Protect Service works? |
| |
This service can be availed by just pointing your Mail Domains "MX" record to our Mail Protect setup. When you sign up for the service, we send you the changes you need to make to the DNS "MX" records for your domain.
Changing MX record: After subscription to Mail Protect services, your MX record is redirected to point to the Mail Protect servers. Thus all the inbound emails to your mail server will be screened for spam, viruses and other malicious codes and then routed to your email server, cleaned and safe.
For your outgoing mails, the service requires you to assign Mail Protect SMTP IP’s in your mail system outbound settings, which will be provided to you after the provisioning is done at GIDC’s end.
|
| 1.8 |
How is the Mail Protect Service offered in terms of plans and prices? |
| 1.9 |
How can I subscribe Mail Protect Service? |
| |
Mail Protect service is available in multiple packages on number of user account basis to suite your specific requirements. Service offers flexibility of taking plan in multiples of 5 email accounts going upto 10000 email accounts or more. There is no further complexity in subscribing the service, as we have already bundled all other options such as Anti-Virus & Anti-Spam protection, Content Filter, Unlimited Data Transfer and Unlimited queue, etc. to provide best of breed email security with utmost peace of mind.
|
| 1.10 |
What are the charges for Mail protect service? |
| |
Mail Protect service is available in multiple packages on number of user account basis to suite your specific requirements. Please get in touch with GIDC Account manager or call our 24*7 Help desk to give you charges and applicable plan meeting your requirement. You can also send us email to that effect on ‘rmp@relianceidc.com’, and one of our account manager will be more than happy to assist you with whatever information you want.
|
| 1.11 |
Are there any other hidden cost such as hardware / software investments or additional charges for service components, features etc? |
| |
No. There are so such costs whatsoever. Mail Protect Service is priced on the number of mailboxes that use the service
|
| 1.12 |
How long does it take to activate the service? |
| |
Activation of your evaluation request will happen in 24 hours and you will receive activation confirmation message from GIDC team with details on rest of the formalities.
Processing of mails at Mail Protect gateway will start after you change the MX pointer to Mail protect setup (after receiving activation confirmation from GIDC).
Please be advised that after MX change, it takes 0-48 hours time for DNS updates globally. Thus all your mails will start getting routed and scanned through Mail Protect platform in 0-48 hours time frame after MX change.
|
| 1.13 |
How can I change my MX record? |
| |
Changing MX record is a very simple activity. Some hosting companies let you change your domain's DNS settings through a control panel. Others require that you submit the requested changes to their technical support department.
* If your authoritative Name Servers are with Global Internet Data Center, then please send confirmation mail to GIDC Helpdesk for effecting change in MX record.
Please be advised that after MX change, it takes 0-48 hours time for DNS updates globally. Thus all your mails will start getting routed and scanned through Mail Protect platform in 0-48 hours time frame.
|
|
|
| 2. Service Feature FAQ’s |
| 2.1 |
Where is Mail Protect setup hosted / placed? |
| |
Mail Protect setup is hosted at our own TierIII+ data center in Mumbai, India. Global Internet Data Center facilities are self-owned, self-contained and positioned in multiple seismically stable zones. Each facility is encased within multi-layered physical and electronic security.
|
| 2.2 |
Highlights of Global Internet Data Center Infrastructure |
| |
A: Secure. Stable. Scalable.
B: Fortified. High redundancy. Robust superstructure.
C: Blazing speed. Uninterrupted. Ubiquitous Access.
D: 24*7 monitoring and management
|
| 2.3 |
What is Mail Protect - Threat Protection? |
| |
Unique Ironport Reputation Filters™ technology identifies suspicious traffic patterns. Suspect senders are throttled or blocked, preventing malicious traffic from even entering or leaving the network.
|
| 2.4 |
What Spam detection tools are used? |
| |
Mail Protect utilises world’s best Gateway Anti-virus Anti-Spam protection technology from Ironport Systems, US. Fully integrated industry leading spam detection powered by Ironport® anti-spam from Symantec as well as Ironport anti-spam engine is used to ensure precisely accurate spam detection.
Compete setup is managed by highly trained dedicated security core team at Global Internet Data Center.
|
| 2.5 |
How do I set the Blacklist / White list (e-mail filters feature) so that I get the e-mail I want? |
| |
You will not have to worry about all these issues as Mail Protect Service is delivered on worlds best and most accurate Spam detection platform. The service offers industry leading accuracy level of 99.9999% with 0.0001% false positive rate. However in case you still need to white list or black list any email account, simply get in touch with 24*7 GIDC Help Desk.
|
| 2.6 |
What virus scanners are used? |
| |
Mail Protect use fully integrated anti-virus engine from Sophos and Ironport Systems. Platform delivers best of the breed virus detection and cleaning technology available in the world.
|
| 2.7 |
What is Policy Enforcement? |
| |
The Service includes the world’s fastest content scanning engine. This flexible engine allows for fine-grained enforcement of corporate policies based on keyword searches of messages or attachments.
|
| 2.8 |
What are the e-mails quarantine policy for Mail Protect Service? |
| |
Spam is quarantined for 15 days. Viruses are quarantined for 30 days.
|
| 2.9 |
What will happen to the mails in case my mail server is down or not reachable from Internet? |
| |
Mail Protect System immediately recognise that your mail server is not reachable to receive incoming mail traffic and will start queuing the mails. As soon as your server is reachable, the system will automatically deliver all the queued messages instantaneously. Mail Protect offers Unlimited queuing for all incoming mails for upto 5 days on highly redundant infrastructure.
|
| 2.10 |
What if my mail setup is down for more than 5 days (Mail Protect default queuing limit)? |
| |
In case you realise that your mail server will take more than 5 days to come up, then you need to notify GIDC Help Desk in writing about the expected number of days of extension you may require for holding the mail queue at Mail Protect end.
|
| 2.11 |
Is service monitored and supported 24x7? |
| |
Yes. Mail Protect service is administered 24x7 by core team of security professionals. You can contact GIDC Help Desk 24x7x365 basis via phone, email or fax, for any assistance or support you may need on Mail Protect Service.
|
| 2.12 |
What is ‘Unique Incident Response System’ – antiabuse@relianceidc.com? |
| |
The Mail Protect layer is super efficient, precisely accurate spam detection and cleaning system, however in rare circumstances, when system is unable to classify a mail between spam and legitimate, then the mail is delivered to the recipient with ‘Suspect Spam’ tag in subject line. Upon validation, if user finds that the mail is a spam, then user can simply forward the same to “antiabuse@relianceidc.com”. GIDC Security Team will attempt to block all similar spam at gateway level, so that in future, user do not receive such spam.
|
| 2.13 |
What is an open-relay server? |
| |
For historical reasons, many simple mail transfer protocol (SMTP) mail servers will accept mail for e-mail domains other than their own, and forward it on to the intended recipient. Any machine that will accept e-mail for any domain and forward it on regardless of who the sender is or what IP address the e-mail is sent from is referred to as an “open-relay” server.
Spammers hunt for and abuse these servers to try to cover their tracks, because they know their spam is unwelcome and unwanted. When spammers locate such a server, they can use it as a free distribution service for their junk e-mail.
|
| 2.14 |
What does open-relay mean to me? |
| |
You must make sure your SMTP server does not allow open-relay, because if it does, it can be used as a spam gateway. This very often leads to your IP addresses and/or domains being blacklisted by anti-spam groups. Most current SMTP servers and firewalls allow you to restrict SMTP relay either by IP number (so you accept mail only from specified IP numbers) or by domain (so you reject mail destined for domains other than your own).
|
| 2.15 |
How will Mail Protect offer security in case my mail server is an open-relay? |
| |
Mail Protect service comes with unique feature of protecting your mail server from all external vulnerabilities. This is achieved by restricting relay service (SMTP port –25) of your mail server from Internet, to ensure that the same is not reachable from outside.
Since your mail system can not relay mails after restricting SMTP port, GIDC provides its own SMTP IP to you for relaying mails. Mail Protect Service extends unique facility of authenticating your users on your own mail server before allowing them to send mails outside.
This functionality may not work in few specific scenarios whereby mail server does not support authentication or have proprietary encryption techniques.
|
|
|
| 3. Service Security FAQ’s |
| 3.1 |
How am I assured of Security of my emails while they are processed at your end i.e. at Mail Protect gateway level? |
| |
Global Internet Data Center’s Information Security Management System (ISMS) ensures the protection of Physical, Software and Information assets against all threats and vulnerabilities that can be exploited deliberately or accidentally by internal or external entities.
At Global Internet Data Center, every possible step is taken to ensure that our setup, procedures, and practices are completely secure. Our ISMS policy ensures compliance with following practices;
- BS 7799 Security Certification
- Confidentiality, Integrity and availability of all the assets is maintained throughout its life cycle.
- Legislative and Regulatory requirements are met (India Legislation)
- Risk assessment is carried for all the assets and applicable security controls are implemented.
- Business Continuity Plans are developed, tested and maintained.
- Information Security Awareness & User responsibilities‘ training is provided to all employees
- Incident Management process reports all actual or suspected security breaches and incidents and is thoroughly investigated to take preventive/corrective actions.
Email is one of the most critical business asset for any enterprise and accordingly, at Global Internet Data Center, we have put worlds best and most secure Gateway Antivirus and Anti-spam infrastructure from Ironport Systems, US.
Few other silent Technical features which ensures complete security of emails while they get processed at Gateway level,
Advance MTA / Queue Design to ensure highest level of security
IronPort has developed a completely new MTA architecture with a unique independent queue design to ensure that the message processing happens at the highest speed and also extends complete security of mails, through out these transactions.
- Queue Security: There is no visibility of Queue on the Ironport setup hence it is not possible to see messages (body or attachment) while these are processed at the gateway level. The maximum visibility is of header information only.
- Message Encryption: All the messages on Ironport setup is encrypted to ensure that messages can not be accessed at any level.
- Powerful & Comprehensive Log management: Gateway setup has very comprehensive log management which captures every movement / action on mail. The logs are default feature and can not be enabled / disabled by administrator. Further the Logs can not be tempered by any manual intervention.
GIDC maintains the log for 15 days for any trouble shooting or inspection. The logs can be provided to customer on need basis for their examination / analysis.
Virtual Gateway – Technology for outbound mail
Virtual Gateway technology allows the system to identify and assign unique classes of mail to unique outbound IP addresses - a very powerful feature for managing issues of deliverability. This helps in separating the outgoing mail for different organisations onto different outbound IP addresses. If any of the different mail streams cause problems with a receiving ISP that leads the ISP to block that mail, the blockage will only be limited to the IP that caused the problem, allowing mail from the other mail streams to flow without interruption. Each customer or set of customers are given unique IP address, ensuring no one customer will impact the mail flow of another.
|
| 3.2 |
Can we perform or assign third party to do Security Audit of Mail Protect Setup at Global Internet Data Center? |
| |
Yes, you can conduct security audit as per your requirement.
No one else can understand the real importance of security as we do, being the custodian of most critical business asset of very large enterprises, MNC’s, Government setup, Banks etc. Clients include leaders in segments like MNC’s, banking, insurance, financial services, government bodies, telecommunications, etc. Many of our large customers have conducted various level of Security audits before placing their setup with us. Apart from customer conducted Security Audits, Global Internet Data Center conducts various audits such as Venerability assessment, security audit, test drills, etc. on regular intervals to ensure complete compliance with security aspects.
|
| 3.3 |
Is it possible to see my mails by Global Internet Data Center staff while they are processed at your end? |
| |
No, it is not possible to see the mails while the same is processed on Ironport Appliances for virus / spam scanning. Further please note the following points;
- Mail processing is so quick that it hardly takes second to leave the systems after cleaning
- The processing happens on multiple Ironport appliances, which are behind load balancers, making it further impractical for any staff member to interfere in mail process
- Throughout processing cycle of mail on Ironport setup, it is encrypted and no visibility is provided to system administrator or any user staff
- No quarantine of mails at Gateway level – To ensure completely same messaging environment, we do not quarantine mails at gateway level except virus mails. Only if recipient mail server is down and can not accept mails, Mail protect system quarantine mails upto 5 days which are stored in encrypted format.
|
| 3.4 |
What if I do not receive some mail, which is sent to me? |
| |
This is quite possible, although very rare, that you may not receive some mail which is marked to you. The only probable reason for such event will be virus infected mail, which system is unable to clean. In this case we quarantine virus-infected mails at our end for 30 days. Upon your request, we can release such mail at your own risk.
Please note that we maintain the mail logs for 15 days. In case you want details on delivery / receipt of any mail for any specific user, GIDC Help Desk team will be able to provide complete information on the same.
Mail Protect service guarantees upto 99.99% uptime, which means near 0 (Zero) loss of mails.
|
| 3.5 |
Is there any backup system in place for all the mails processed by Mail Protect? |
| |
No, as processing of mails at Mail Protect setup happens at flick of seconds, it is not required to do any backup. The complete setup is deployed in high availability mode ensuring 99.99% uptime. Further our security practices does not allow us to store customer mails without specific / separate subscription of backup services under separate order.
|
|
| 4. Spam Digest FAQ’s |
| 4.1 |
What is Spam Digest? |
| |
Digests are a summary of suspected spam mails which is sent to end users of the domain.
The list of all mails which are quarantined for the respective user is sent as a digest mail so that the end user can release any mail if it’s found to be genuine. Once the mail is released it will get forwarded to the end users mail box. The duration for sending these digest mails can be chosen by the administrator.
Advantage
The advantage of ‘Spam Digest’ options is that the user need not login to any interface to check for mails. He can directly release his mails from his Mail client and also he would receive only one summary mail which contains the list of all suspected spam mails. The mail client should support HTML format. This is considered to be an efficient way to monitor your spam box.
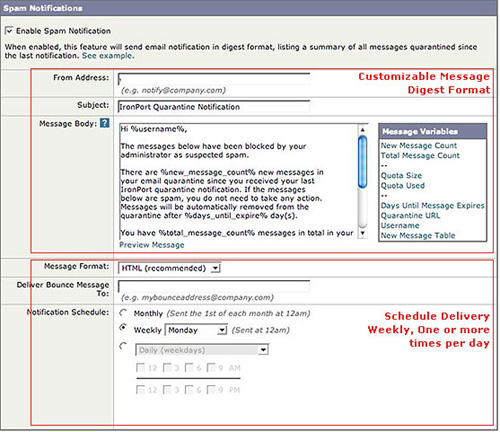
The above mailer as customised will go to the end user with the summary of all “Suspected mails” as shown below.

Once the mail is released from the Digest the same will update the necessary databases and will be delivered as a normal mail to end user Mailbox.
|
| 4.2 |
I’am not receiving any spam notifications. Why? |
| |
The system will not send a notification if there are no spam messages received since the previous notification. Your administrator will set the frequency of these notification emails.
|
| 4.3 |
Why am I getting multiple notifications? |
| |
Your administrator may have installed more than one quarantine system and each is sending a notification of messages it has stored. If you have or use more than one email address, you may also receive notifications for each of these email addresses.
|
| 4.4 |
Do I need to delete messages that are spam? |
| |
No. Messages that are spam need not be deleted. The system will automatically delete older messages, typically those older than 14 days. You will not receive notification of messages that have been listed in a prior notification.
|
| 4.5 |
Can I review older messages? |
| |
Yes. You can review any messages held in quarantine that have not yet been automatically deleted due to age. Click on the “your email quarantine” or “View All Quarantined Messages” link in the notification.
|
| 4.6 |
I still have an old notification email. Can I use this old notification to manage spam messages? |
| |
Yes. Any notification received can still be used to manage messages, or to navigate to the web interface of the spam quarantine provided the mail has not been deleted or released.
|
| 4.7 |
I attempted to release a message but reached an error page that says, “This message was not found. It may have been released or deleted.” I have never released or deleted this message. What happened? |
| |
If a spam message was delivered to a mailing list address, the notification will be delivered to all the email addresses on that mailing list, and any user with the notification can release or delete the message.
|
| |
|
|
| |
|
|
|
|
| |
| Why Global Internet Data Center? |
| |
| State-of-the-art facilities |
 |
| Redundant connectivity |
 |
| Managed services |
 |
| Expertise across platforms |
 |
| Customer care at its best |
 |
| Strategic alliances |
|
|
|